|
|
Security Center
HLSB Quarterly Customer Newsletter Issue 3 |
|
Beware of Scams! |
|
HLSB Quarterly Newsletter Issue 02 |
|
Q1 Home Loan Customer Newsletter |
|
How to Safely Use Mobile Payment Apps and Services |
|
The Threat of Ransomware |
|
Spotting Malicious Links |
|
Internet Safety |
|
Information Oversharing |
|
Online Security Basics for Business |
|
Blocking Mobile Attacks |
|
Online shoppers continue to engage in risky behavi | Findings
from a new McAfee survey reveal the risky habits of online shoppers, including
using unsecured
Wi-Fi for online shopping and purchasing items
from online retailers they are not fully confident are genuine (51 percent).
This highlights the need for consumers to slow down and consider the risks of
unsafe purchasing behavior that could lead to identity theft or financial loss. 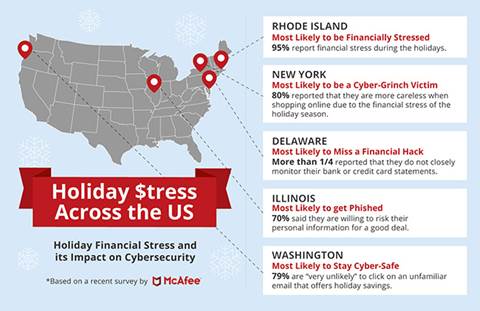
Last year
consumers spent $453.46 billion on the web for retail purchases, which was a 16
percent increase over 2016. Unfortunately, when it comes to online shopping,
consumers are more concerned about finding the lowest price than potentially
jeopardizing their personal cybersecurity in the process.
The survey
found that 56 percent of consumers are willing to use a website they are
unfamiliar with, if this means they can save money on their purchases. Even
worse, 31 percent admit to clicking links in suspicious emails for better
deals.
“For most
people, the holiday shopping season is a stressful time of year, especially
from a financial perspective. With added stresses and distractions, people
often let their guard down when it comes to their digital security, which can
lead to risky consequences,” said Gary Davis, chief consumer security
evangelist at McAfee. “Cybercriminals know that people are less focused on
security measures during this time and use that to their advantage. By taking
the proper steps to protect themselves and being wary of deals and offers that
appear to be too good to be true, consumers can enjoy a safe holiday season.”
The
United States of Online Shopping
The McAfee
survey also examined cross country behaviors, identifying the states that
exhibit the safest online behavior. Residents in Washington are most likely to
stay cyber-safe during the holidays, with nearly 80 percent of respondents
claiming they are very unlikely to click on a link in an unfamiliar email.
Conversely,
New York residents are the most likely to fall victim to a cybercriminal, with
80 percent claiming that they are more careless when shopping online due to the
financial stress of the season. Shoppers in Delaware reported that they do not
monitor their bank and credit card statements during the holidays, while 70
percent of survey participants in Illinois noted that they are willing to risk
their email addresses, phone numbers, home addresses and bank account details
for an online deal.
The states
where residents are most likely to fall victim to a cybercriminal are:
1. New
York
2.
Illinois
3. New
Mexico
4. Kansas
5.
California
The states
where residents are least likely to fall victim to a cybercriminal are:
1.
Washington
2. South
Dakota
3.
Minnesota
4. Nevada
5. Hawaii
Tips for
consumers
Connect
with caution. Using public Wi-Fi might seem like a good idea in the moment,
but if consumers are not careful, they could be unknowingly exposing their
personal information or credit card details to cybercriminals who are snooping
on the network. If public Wi-Fi must be used to conduct transactions, use a VPN
to help ensure a secure connection.
Think
before you click. One of the easiest ways for a cybercriminal to target victims
is by using phishing emails disguised as holiday savings or shipping
notification, to lure consumers into clicking links that could lead to malware,
or a phony website designed to steal personal information. Instead of clicking
on a link in an email, it is always best to check directly with the source to
verify an offer or shipment.
Browse
with security protection. Use comprehensive security protection that can help
protect devices against malware, phishing attacks and other threats.
Use a
tool to help protect your personal information. Use a solution that
takes a proactive approach to help protect identities with personal and
financial monitoring and recovery tools to help keep identities personal and
secure.
|
Employees aren’t taking the proper steps t |
ObserveIT
surveyed more than 1,000 U.S. employees ages 18 – 65+ who have traveled with corporate
devices in the past year and found that the majority are putting connectivity
and efficiency above security; using public Wi-Fi and unauthorized devices to
access work email and/or files on the go.
While they
may not have malicious intent, the negligent actions of employees caused 64
percent of all insider
threat incidents in the past 12 months (Ponemon
Institute). And, though breaches caused by accidental insiders can happen at
any time, there’s heightened risk when employees are outside the office, using
public workspaces or personal devices to remain connected.
The survey
confirms that employees are, in fact, jeopardizing corporate information while
they’re traveling, and employers aren’t doing enough to mitigate these risks.
Connectivity
is valued more than security
More than
three fourths (77 percent) of respondents say they connect to free or public
Wi-Fi while traveling. Further, with 63 percent of people saying they’re using
public Wi-Fi to access work emails and files, they’re presenting an easy
opportunity for cybercriminals to infiltrate and exploit sensitive data.
Organization-wide
guidelines are unclear
Organizations
aren’t doing enough to educate employees about cybersecurity best practices.
Almost half of those surveyed (49 percent) said they’re either unaware of any
organization-wide travel-related cybersecurity guidelines, or, their company
doesn’t have any. This can result in employees engaging in risky behavior – for example, only 17 percent of
respondents said they always use a VPN to connect securely outside the office.
Holiday
travel poses additional risk to organizational security
The survey
also found that 55 percent of people plan to bring a work device along with
them while traveling this holiday season. As the data indicates, people
value convenience over security, so creating
cybersecurity awareness around year-end travel will be critical to ensuring
sensitive data isn’t leaked unintentionally.
“Not only
does this research confirm that cybersecurity isn’t top of mind while employees
are traveling, but it also highlights a major gap in security awareness
training around mitigating the threats posed by remote work,” said ObserveIT
CEO Mike McKee. “While technology has enabled people to be productive regardless
of location, it’s also creating new ways for hackers to infiltrate otherwise
secure systems. Organizations can’t just focus on what’s happening within their
four walls. Rather, they need to take a holistic approach that puts security
first, wherever work is getting done.”
|
5 Common Cyber Threats (and How to Fight Back! | High-tech
threats are everywhere, from the data breaches at retail stores to the Internet
security issues like the "Heartbleed" bug that's dominating the
nightly news.
But
a little knowledge, and common sense, can go a long way toward helping protect
you from identity theft and financial loss.
Phishing
An email that appears to be from your
financial institution or another business you deal with asks you to click a
link that directs you to a web page that looks legitimate. On this web page,
you may be asked to verify personal information, such as your account number,
password or Social Security number. The email may include an attachment, which
it urges you to open.
Don't bite. It's a scam to snatch your
personal data. HLSB and other reputable companies never gather information this
way. If you are suspicious of an email from HLSB, forward it to admin@hlsb.com, then permanently
delete the message.
Vishing
Think of this as phishing over the phone. The
"v" is for voice. Instead of sending a bogus email, the criminals
call you, claiming to be from your bank or another institution you trust, such
as the local court system calling about jury duty.
Even if an email or phone call appears to be
legitimate, be suspicious. If they ask for a Social Security number or other
personal information, think twice. Hang up and call the organization's customer
service number to double-check.
Smishing
This variant of the phishing concept uses
text messages to lure you into clicking links that provide your personal
information or download infected apps on your phone.
Don't respond to text messages or automated
voice messages from unknown or blocked numbers on your mobile phone.
Internet Safety
Pop-up ads are especially bad, since clicking
on them could trigger your computer to download a nasty virus or spyware software that gathers personally identifiable
information, including email addresses and passwords, from your computer without
your knowledge. The same goes for attachments or links that come in unsolicited
emails or in unsolicited Facebook, Twitter or other social networking
messages.
Once a malicious code is on your machine, it
can hijack your computer's operating system, send spam and malware to other
computers, launch unrelenting pop-up ads, or even record your keystrokes and
report back to its controller.
Defend your computer with anti-virus,
anti-spam, anti-spyware and pop-up blocker programs: Also consider researching
alternative browsers that utilize additional security features. Remember, when
you're in unfamiliar territory on the Internet, trust no one.
Laptop/Phone/Tablet Theft
It may sound old-fashioned and boring, but
theft of devices remains the most common computer crime because it requires
zero know-how to pull off. Tablets are increasingly popular as they are easily
resold on the black market.
To help protect yourself, use a laptop cable
lock whenever possible, and keep important gear out of sight unless you're
using it. Store briefcases in your trunk, not the passenger seat of your car,
and make sure you use strong passwords and encryption (if available) on all
your devices in case they fall into the wrong hands.
|
The Dangers of 3rd Party App Stores | According to sources
like the NY Daily News, CNN, and CNET, more than 90% of Americans now own
cell-phones, and roughly 50% of those phones are ‘smartphones’, capable of
accessing the internet and running small gaming and productivity applications
known as ‘apps’.
With a 90% market
penetration, chances are you’ve probably heard all of that before. But just in
case, now you know.
As with any widely
adopted technology, there always follows a plethora of individuals seeking to
misuse said technology for less-than-ethical personal gain. Companies
like Kaspersky Labs, Avast and McAfee who provide mobile antivirus solutions
have reported a sharp increase in mobile malware attacks within the last year.
These attacks range from stealing and/or damaging private information to
hijacking other applications, and even taking complete control over a user’s
phone and placing calls, sending SMS messages, turning on the phone’s
microphone or cameras, spamming contacts, or simply locking the user out, and
holding the device hostage until a ransom is paid.
When it comes to mobile
malware, the attacks are widely varied, and seemingly limited by nothing more
than the hacker’s imagination. However, there do seem to be some common threads
in the attacks:
1) The majority of
mobile malware attacks appear to target Android based devices by quite a
significant margin.
2) Apple devices are
rarely infected unless the device is jail-broken.
3) Roughly 99.86% of
malicious or infected apps are downloaded from third party app stores (app stores
other than iTunes and Google Play).
4) Mobile Antivirus
solutions appear to do a pretty decent job of combating most infections.
These statistics do not
mean that everybody should throw their android devices in the garbage and go
buy an Apple i-something. In fact, the current estimated infected device
percentage for the U.S. Market is still thought to be less than 1%. However,
experts agree that this number is growing.
So what should you
do?
Exercise caution with your
mobile device. If you are going to download an app, try to do it from the
recommended app store for your device (such as iTunes or Google Play). If
you absolutely have to have an app from a third party store, take time to
research the app and read reviews
|
USA Today Money | Using Debit vs. Credit |
|
Refresher: Protect Mobile Data | 
Be a human firewall!
Laptops, smartphones, tablets, USB flash drives, and even digital cameras can be used to store data. There are two key risks you take when storing data on a mobile device. The first is that you could lose that data if the device is lost, stolen, or damaged. This could include contact information, important files, email messages, and more. The other larger risk is that any sensitive information on the device may be exposed to the public, possibly exposing clients or employees to identity theft or other forms of attack. Such incidents could be covered in the press, becoming a public relations nightmare. Whenever using a mobile device, follow these best practices: - Always use a strong password,
- Only place sensitive information on a mobile device if it is absolutely necessary, the device can protect it, and the device is approved for business use,
- If you must store sensitive information on a mobile device, consider encrypting the data, which is a way of electronically locking it. Contact your business' IT administrator for assistance,
- Backup key data stored on mobile devices regularly and store that data in a secure location, and
- Be on guard against thieves looking to steal your mobile device and use a cable lock for laptops.
|
Sharing USB Drives Can Be Risky | |
All USB
devices share a common and potentially harmful flaw. Hackers know that
computers are typically set up to listen for what type of USB device is plugged
in. This means that criminals can reprogram USB devices to pretend to be
something other than what it really is. That device can then be used to
spy on you, capture passwords, or do permanent damage to your system. This
activity goes undetected by antivirus programs since it is not a running
program but actual hardware.
This potential risk is called USB
duping and the only complete safeguard against potential infection is to
disable USB ports altogether. This practice has already been implemented by the
U.S. military in sensitive areas, along with banning all USB drives. Awareness
is the most important factor in thwarting an attack of this type, so remember
to be wary of strangers asking to charge a cell phone or borrow a USB drive.
|
|
©2012 Home Loan State Bank • Member FDIC - Equal Housing Lender

Home •
About Us •
Personal Banking •
Business Banking •
Online Banking •
Contact Us
Privacy Policy |
Patriot Act |
Disclosures |
2025 Bank Holidays
*Remember to never transmit sensitive personal information through unencrypted email or an unsecured internet connection!*

|
|



